Author: Giancarlo Parodi, Principal Engineer, Renesas Electronics
The growth of connectivity-capable devices implies a greater need to secure both communication channels and any local storage that the device may use, to protect the confidentiality and integrity of user data. Therefore, a developer of embedded devices must consider how to implement the required functionality for the needs of current users and how to make the implementation future-proof to meet future requirements in a cost-effective manner. A security roadmap must strike the right balance between addressing the current (and legacy) approach, making the implementation compatible with the end-equipment lifecycle, and being open to enhancements that may arise in the future.
One of the most challenging aspects is the management of users' cryptographic keys, from the production phase and later in the field, since they are the most sensitive assets to protect, from the perspective of the end user. This article describes how Renesas can help its clients meet such challenges in an easy and cost-effective manner.
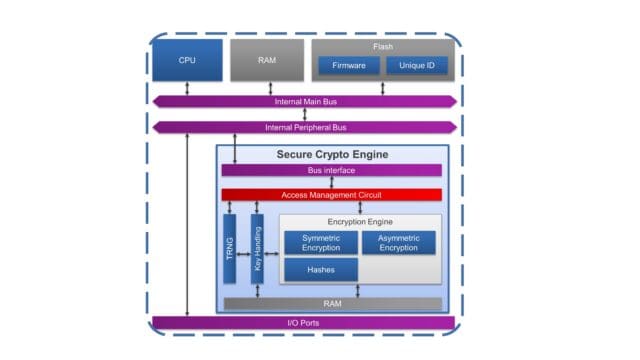
Keys need to be protected in various threat scenarios: during installation on the system, during use, when stored on the device, and after the equipment is disposed of. To facilitate all those requirements, it is a great advantage if the microcontroller includes a dedicated subsystem that is designed to autonomously take care of all those aspects. Fortunately, this is the case with the RA family of microcontrollers, which includes the Secure Crypto Engine (SCE).
The SCE-defined secure subsystem (depicted in Figure 1) provides comparable secure element functionality with much higher performance as an integrated solution, reducing BOM cost and simplifying integration both in the development stage and in the production. It supports AES, RSA, ECC, Hashing, and true random number generation within an isolated on-chip environment. In addition to this, the SCE enables secure storage of unlimited keys using a factory-programmed 256-bit Hardware Unique Key (HUK) to derive "key encryption keys", which in turn can be used to wrap (encrypt) any supported client key type. The Secure Crypto Engine (SCE9) cryptographic subsystem is completely contained and isolated within the MCU, and protected by an access management circuit that shuts down the operation of the cryptographic engine upon detection of illegal access attempts. The SCE performs all plaintext cryptographic operations using its own dedicated internal storage area, which cannot be accessed via any CPU or DMA accessible bus. The advanced key storage and key management capabilities of SCE9 can ensure that plain text keys are never exposed or stored in CPU-accessible RAM or external non-volatile memory.
The RA family of microcontrollers includes the SCE in all connectivity-capable groups, such as the RA6 and RA4 derivatives. The RA6M4 is the first MCU in the RA family in Renesas' new generation of security-focused MCUs. State-of-the-art security features combined with best-in-class IP peripherals and pin and feature compatibility across the MCU series make the RA family MCUs the optimal choice for almost any connected embedded product.
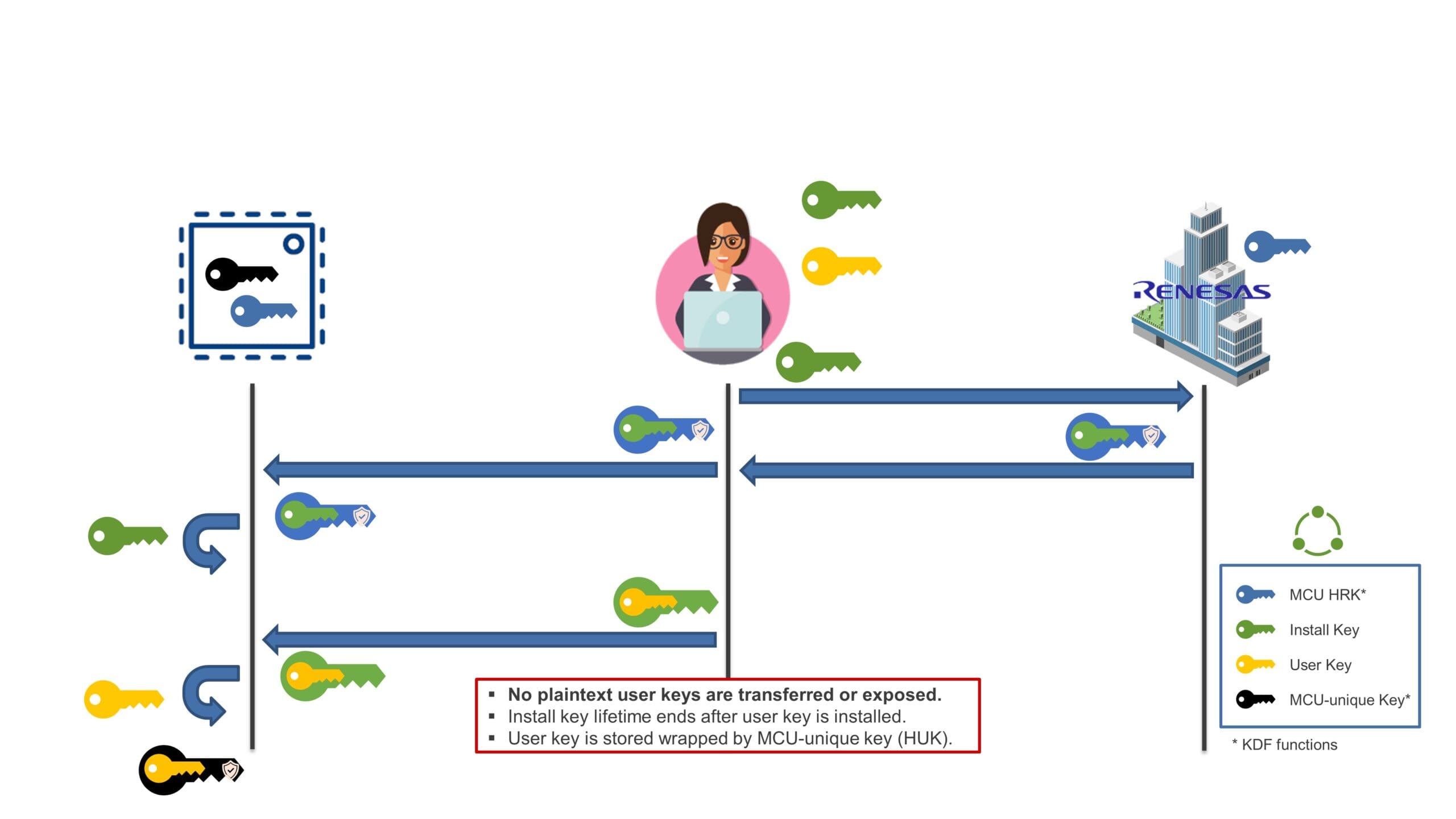
All Renesas MCUs support factory programming via serial and USB interfaces as a low cost and reliable mass production mechanism. In addition to this, the built-in functionality of the RA6M4 and subsequent series of microcontrollers allow users to implement secure key provisioning through the same programming interface. The MCU boot firmware supports a dedicated command protocol to pass a chosen installation key and an encrypted payload (the application key is injected) to the SCE boundary; the application key is generated in a wrapped format unique to the MCU that can be stored securely in non-volatile memory.
Since both the key installation key and the user application key are encrypted, there is no need to use a hardware security module (HSM) or secure programming service for user key injection in production . Renesas provides a free “Off-line” service to all of its customers to generate the necessary factory-installed key data payload, through a dedicated infrastructure called a Device Lifecycle Management (DLM) server. The entire communication between the user and the server is secure and encrypted via PGP; notably, the application key is not exposed to the DLM server itself at any time.
The user application can take advantage of the SCE capability through dedicated cryptographic drivers, included in the Renesas Flexible Software Package (FSP). The FSP is an enhanced software package designed to provide high-quality, scalable, and easy-to-use software for embedded system designs using RA microcontrollers. Supports Arm® TrustZone®, advanced security features, provides production-ready, low-memory, high-performance controllers, integrates middleware stacks such as Azure® RTOS, FreeRTOS™, making it easy to deploy complex modules for communication and security.
As for SCE drivers in particular, they implement two modes of operation, called "compatibility mode" and "protected mode".
Compatibility mode
One of the main reasons for their existence is that many legacy systems require handling plaintext keys, or real implementations need to integrate with different stacks and libraries that do not natively handle wrapped keys (sometimes called "key blobs"). . The SCE is flexible and can support plain text key operation by allowing the application software to import a plain text key at the SCE boundary. After this step, the application could safely store the packed key version in memory, reducing key exposure. In this sense, SCE's secure storage and key wrapping functions become transparent to the end-user application and enable seamless integration with legacy systems or any third-party software and solutions, while offering its unlimited performance and benefits. secure key storage. The application software can use the plain text or encapsulated keys via the PSA Crypto and MbedCrypto APIs.
Secure key storage is virtually unlimited, as any program or data flash location available on the MCUs can be chosen as the storage location. At the same time, the unique hardware key involved in the wrapping process prevents illicit key cloning and copying.
In this mode of operation, the user also has the option of generating encapsulated (random) keys on the MCU itself. This could be interesting to encrypt local MCU data (for example). Also, support for plain text keys could make it easier to integrate with existing programming systems.
On the other hand, the developer should assess the threat of tampering with plaintext keys on the system, especially during operation, as the key content will be exposed outside of SCE boundaries. This risk affects both the operation of the software and any subsequent key updates, when malicious code could exploit weaknesses in existing software to obtain the key data.
Protected mode
This provides a significant improvement in both system-level security and secure key handling, by implementing a best practice approach. In this mode, only natively wrapped keys are allowed and the system does not support the operation of plain text keys. This completely eliminates key exposure from the CPU, DMA, or other system bus interfaces and dramatically reduces the attack surface.
As in compatibility mode, the SCE can generate wrapped (local) keys.
Known user keys can be securely installed by a device programmer interacting with on-chip boot firmware, enabling secure key provisioning in production. These keys are securely stored in a wrapped format and can be used directly in the application. The same interface can be used to factory-install key-update-keys, that is, keys that application software can use to securely update and update application keys in the field. This in turn means that there is no dependency on the DLM server service after the initial factory programming has been completed.
In addition to this, the protected mode allows various countermeasures to protect the system against simple and differential power analysis attacks (so-called SPA and DPA). Such attacks imply that the operator has physical access to the system (such a threat can be mitigated by other security policies, depending on the operating environment), however they are becoming cheaper and faster to implement and therefore it is important protect against them.
Similarly, countermeasures against timing attacks are implemented for ECC and RSA crypto operations, which are handled in constant time when dealing with sensitive key material (to prevent timing side channel leakage).
SCE protected mode can be accessed using the "FSP Crypto" module in a standalone format, as part of the FSP package. Although integration with legacy systems and software may require an architectural redesign, it is worth considering the benefits provided by the protected mode of operation.
For applications that want to use the Trusted Firmware-M (TF-M) implementation of a secure processing environment for Arm® Cortex®-M33 architectures, SCE compatibility mode can be used in combination with PSA cryptography and integrates seamlessly with existing ARM PSA exosystem software. This integration is provided as part of the FSP package.
Additionally, the FSP can use compatibility mode to integrate with Amazon FreeRTOS, including support for MbedTLS, or support for Azure RTOS and NetX Duo.
Other connectivity solutions, such as the commercially supported WolfSSL integrated SSL/TLS library stack, can take advantage of protected mode operation and are currently under development.
In short, Renesas solutions can support any application security roadmap, from supporting existing and legacy systems, to providing the foundation for an enhanced security path to optimal protection of user assets and applications.
The described software and functionality is available in the RA family of MCUs, beginning with the RA6M4 MCU and the upcoming RA33 and RA6 series Cortex-M4-based microcontrollers.