“Everything starts with trust” – said the advertising slogan of a German bank. The ability of a person or a system to respond in a predictable way, even under highly stressful conditions, builds trust. However, the more valuable the assets or data and the more complex the systems, the more difficult it is to guarantee this claim. The same is true of embedded systems.
The number of embedded devices is growing exponentially, accompanied by a disproportionate increase in the risks to which they are exposed, especially with the integration of networking capabilities. The level of risk increases with each layer of integration, for example, in Industry 4.0 Cyber-Physical Systems (CPS). As soon as they have had core functionalities, they have migrated to the cloud (cloud), where new threats emerge. This happens because the cloud removes the protection that the physical separation of devices used to offer. Until now, there have been no scalable security tools that mobile network operators could use to verify that their data and EDP systems remain confidential and free from harm. As a result, software components located in the Cloud must be protected. To ensure interoperability between different devices and systems, the security of the computing platform has to be based on defined standards.
Three Levels of Security
Security can be set at three levels:
• Only at the software level: The presence of these security mechanisms in the operating system is virtually free, but offers limited protection.
• Software and hardware: A reliable execution environment, made up of software and hardware, provides medium protection at low cost.
• Tamper-proof hardware and software: A permanently installed, hardware-implemented secure item equipped with encryption algorithms requires some investment, but instead guarantees the highest level of protection. A wide variety of computing technologies are available for this purpose:
• The Trusted Platform Module (TPM) is a trusted hardware system with a saved key.
• Trusted Network Connect (TNC) describes an access control system that includes security all the way to end devices.
• Self-Encrypting Drive (SED) refers to hardware encryption with precisely graduated blocks.
• PC client, mobile and automotive applications are based on, for example, profiles from the TPM 2.0 Library specification. This also requires a reliable computing platform with interfaces across numerous platforms. It should cover both embedded systems such as Smartphones, vehicles, clouds, virtual machines, servers, desktop computers, laptops and Tablet PCs, and many more devices. For each application, it is necessary to evaluate the degree of protection that the data demands. This is so because security always has a price and the following equation applies: “low investment = low protection”. Therefore, the objective is to find the balance between costs and risks. For example, minimal protection may be sufficient when connecting a set of Bluetooth headsets to a Smartphone. However, the safeguarding of smart meters (smart meters) or tachographs against sabotage requires greater measures, while M2M projects, among others, require maximum protection. Trojan horses, such as rogue servers and clients, and secret mirroring (for example, unauthorized copying of data in hubs), pose the main threats, and not just in commercial applications. They endanger the Intellectual Property (IP) or the know-how of a company and its business model. This can be prevented by taking appropriate measures to maintain quality and reliability and, as
consequently, the positive image of the company.
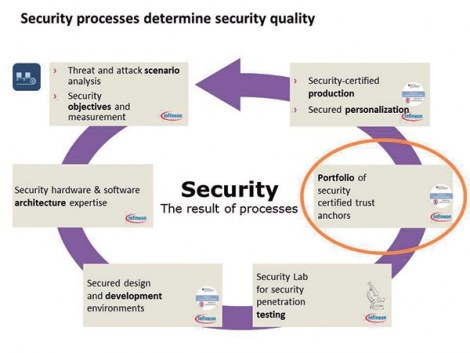
Security Processes
First of all, the quality of security depends on the corresponding processes. In the best of cases, this type of process operates in a repetitive way: it begins with the analysis of attacks and threats, from which the security objectives and the measures to be taken are extracted. This is the basis for establishing the security plan and the development environment and becomes a laboratory that performs tests so that companies can develop certified trust anchors and, consequently, guarantee secure production and customize the final products. Naturally, threats and attacks will continue to evolve, which means that they must be regularly reviewed and analysed: the consequence is that the process starts all over again.
Trust Points
The key aspect regarding the security of a system is the key used to encrypt and decrypt sensitive data. If the key is “hacked” or “cloned”, any security offered is removed. This means that the way the key is managed during the product life cycle – including production – is critical. Three points of trust (trust anchors) guarantee the security of the key: secure storage of the encryption protection, as well as the management of the key itself – in other words, who has access, when and by what means. These points can be implemented in the system in different ways, as a software component of the operating system or as hardware in a separate system with enhanced security features. Although isolating and/or encrypting all data and systems provides extremely high security, this approach is generally not feasible or advisable. For example, a server cannot be encrypted if business partners require access to open data.
Software and firmware updates must also offer a sufficient degree of openness. A typical secure industrial control system might look like the following: A wireless sensor with an embedded encryption module connects to a control unit via one-way authentication. The control unit is equipped with an authentication IC, which is a hardware module with a saved key. With this key, the drive can verify the authentication of the sensor by a second one-way check with another connected part that contains the same encryption module as the sensor. The control unit is securely connected to the sensor and external equipment via a second path. Ideally, the server to which the control unit is linked should also have an authentication IC – as only then is it fully securely implemented and therefore the system truly secure. Apart from allowing mutual authentication between the control unit and the server, it also provides access control and, with it, a secure channel for data transmission, updates and cycle management
of life. In collaboration with Infineon, Rutronik offers modules for every level of security required and all degrees of system complexity found in the industry.
These modules benefit from Infineon's many years of experience in all things security in a wide variety of markets. Numerous smart cards, such as credit, electronic identification, health or access control cards, and the encryption used in pay television services are also based on technologies from this manufacturer, such as Smart Meter, M2M applications, TPMs and secure elements. embedded. Infineon's OPTIGA family enables user and system authentication and secure data exchange. Like a safe, microcontrollers store the security key, certificates, passwords, and data. By doing this, they ensure system and data integrity, so users can be sure that neither their systems nor their data will be corrupted.
They also ensure software and firmware updates. All family members can be personalized with specific keys and certificates. For example, OPTIGA Trust and OPTIGA Trust E are supplied ready for immediate use. The OPTIGA Trust is assigned to an individual 10-byte ID, the uniqueness of which is guaranteed by a unique pair of keys. Its security chip uses state-of-the-art asymmetric Elliptic Curve Cryptography (ECC) to generate encryption codes, which it stores in protected memory. This single chip solution represents an extremely efficient and economic alternative in those applications that only require a low level of security. The OPTIGA Trust E – SLS 32AIA offers a higher level of security and enhanced functionality. Its high-end driver incorporates ECC256 and SHA256. It is also characterized by secure memory and cryptographic functions to authenticate and exchange certificates. OPTIGA Trust P and OPTIGA TPM meet the strict requirements with certification according to CC (Common Criteria) EAL 5+. The Trust P supports ECC521 and RSA 2048, as well as AES, TDES and SHA cryptography. Consequently, it enables both authentication and key generation and change, secure updates, system integrity, and access and lifecycle management. Thanks to the programmability, all functions can be adapted to the needs of different network systems.
The OPTIGA TPM SLB 96xx corresponds to the TPM v1.2 and 2.0 standards and provides certified platform protection for software and data of even the most complex systems at the highest level. This includes strong platform and user authentication, a random number generator (RNG), a tick counter, and a directory of thwarted attacks, as well as built-in algorithms, including RSA, ECC, and SHA-256. Physically separated from the main processor, the OPTIGA TPM can withstand logical and physical attacks. And despite its comprehensive functionality – like all modules in the OPTIGA family – it is a turn-key solution that is easy to integrate and manage. Infineon and Rutronik work closely on selecting the optimal solution for each application and its implementation. In terms of security, this cooperation is of great importance, since the security chips are supplied with pre-programmed and pre-certified key from Infineon. It is essential that this key is secure against possible access on the way to the client. For this reason, Infineon ships the chips as a closed system that Rutronik ships directly to the customer itself.
If necessary, in case of complex applications, there is also the support of a certified integrator from the Infineon partner network, which offers support in the infrastructure implementation process. All relevant security actions are regulated between suppliers, customers and Rutronik by means of confidentiality agreements (NDA – Non-Disclosure Agreements). Rutronik also supports customers' development environments with all available tools to ensure rapid familiarization with the security issue.